Yesterday morning I was checking out my Twitter feed, when I encountered a rather disturbing one
https://twitter.com/j_aksim/status/905742429294342144You can read the whole article here [1].
For those who don’t know who Maria Johnsen is, and are too busy to read the article: she’s a SEO expert who’s trying lately to promote herself as a cyber security expert.
Whether she’s a good or bad SEO expert is not up to me to say but, as a software developer with a deep interest in cybersecurity, who’s also following lots of researchers and malaware analysts, I felt the moral obligation to write something about it.
Even if I didn’t post anything in the past four years.
Even if I probably have now just one visitor/month [2].
Why you may ask? Because, if I will manage to convince even one visitor to switch his/her website to SSL/TLS, I know I made the internet a better and safer place, even if just a bit 🙂
Open letter to Maria Johnsen
Dear Maria,
I saw this comment of yours in one of your latest posts
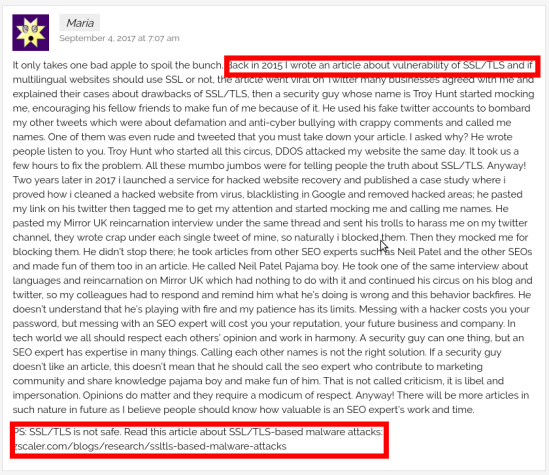
Now, despite what may or may not happened between you and Troy, let us all start to behave like adults, shall we? Thus..
Please stop spreading the misconception that SSL/TLS is not safe by posting links about SSL/TLS malaware attacks, because:
- you’re persuading your users that SSL/TLS is unsafe
- you’re demonstrating that you didn’t even read that article (which I kinda hope so, otherwise it would mean that you didn’t even understood it)
- last, but not least, you’re making a fool of yourself to the people that have a bit of understanding in cybersecurity/software engineering
I couldn’t find the article you mentioned but, judging by the year (2015) and the topic (SSL/TLS), I’m pretty confident you were talking about the infamous Heartbleed bug in OpenSSL happened in 2014. Quoting from Wikipedia (emphasis mine)
Heartbleed is a security bug in the OpenSSL cryptography library, which is a widely used implementation of the Transport Layer Security (TLS) protocol […] TLS implementations other than OpenSSL, such as GnuTLS, Mozilla’s Network Security Services, and the Windows platform implementation of TLS, were not affected because the defect existed in the OpenSSL’s implementation of TLS rather than in the protocol itself.
in layman terms: the math behind SSL/TLS is, as of today, secure: it’s just how SSL/TLS was implemented in OpenSSL that had a flaw. And the proof is that other SSL/TLS libraries were unaffected by this bug (and as of today, there are 17 other libraries implements SSL/TLS).
Now, let’s move to the article that supposedly explains how SSL/TLS is unsafe: you got it completely, utterly wrong. And I don’t even understand how’s that possible, since this paragraph explains it all:
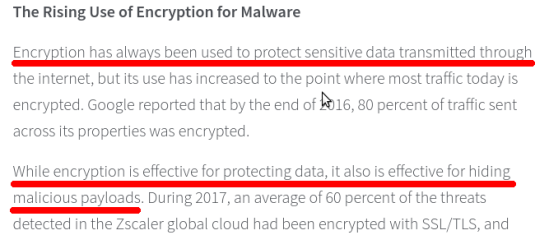
in layman terms: (SSL/TLS) encryption is so good at its job of keeping user’s data confidential, that now even malaware authors are using it to hide their nefarious intents.
Does that mean that SSL/TLS is unsafe? Hell no.
Does that imply that websites using SSL/TLS are unsafe? Hell no.
SSL/TLS is merely a protocol to exchange data in a secure way. Period.
Websites and browsers use SSL/TLS to ensure nobody between the website and your browser (ISP providers, CDN providers, governments, your Company’s IT manager, etc…) can peek into your personal data.
But of course, being SSL/TLS just a protocol, nothing prevents you to write your own software that sends/accepts SSL traffic. Here’s an example. And of course, hackers decided to use it in order to hide the data their malawares exchange.
Does that mean that websites using SSL/TLS are 100% safe? Hell no, never trust anybody selling you the concept of absolute security while saying, few lines below, “governments websites have been hacked too” because indeed, websites can get hacked and, if that’s case, it’s game over for user’s privacy.
But the likelihood to have your privacy stolen is just much more higher if your website does not provide SSL/TLS, because anybody between you and the website can see what you’re doing and, even worse, can manipulate the data without the user, or the website owner, even noticing that. Why? Because it’s not bloody encrypted! Is it that difficult to grasp? Example: some hotels injected custom advertisements in websites that weren’t SSL-enabled.
So, rather than spreading FUD about SSL/TLS insecurity please, be responsible and do the opposite: promote SSL/TLS anywhere, even if the websites don’t handle sensitive data; in this way you’re saying “nobody will easily read/tamper the data between the website and the user, insert custom content, or perform MiTM attacks”.
Best regards,
Diego
Conclusion
Perhaps Maria is good at SEO, judging by the number of followers she has on Facebook, but she also lacks of an understanding of security/privacy and, even worse, she’s not willing to admit it.
There’s no reason to favor non-secure websites against secured ones, and whoever is telling you otherwise, is exposing his/her clients and client’s user base to unnecessary threats.
Her lengthy, whining, childish, overreacting comments against Troy Hunt are a sign of something referred in psychology as Dunning–Kruger effect:
a cognitive bias wherein persons of low ability suffer from illusory superiority, mistakenly assessing their cognitive ability as greater than it is. The cognitive bias of illusory superiority derives from the metacognitive inability of low-ability persons to recognize their own ineptitude.
Look ‘ma, I’m an expert.

1: It’s quite a funny reading: 50% of the post is not about SEO/security at all, but rather, she’s self-promoting her book, basically explaining how she knows better about search engines than Google’s, whose search algorithm is primitive 😀 .↑
2: after posting this article, I actually had a look at my stats and I have to say, after four years of inactivity, I’m impressed I still have visitors stopping by: apparently, my Latex thesis template and how to build an executable library are still interesting. ↑